A new brute force WordPress bot
Over the past week, I've seen a new WordPress bot begin hitting sites that I had not previously been seeing.
It was somewhat subtle, but I noticed my web-05 server being under a higher load than usual.
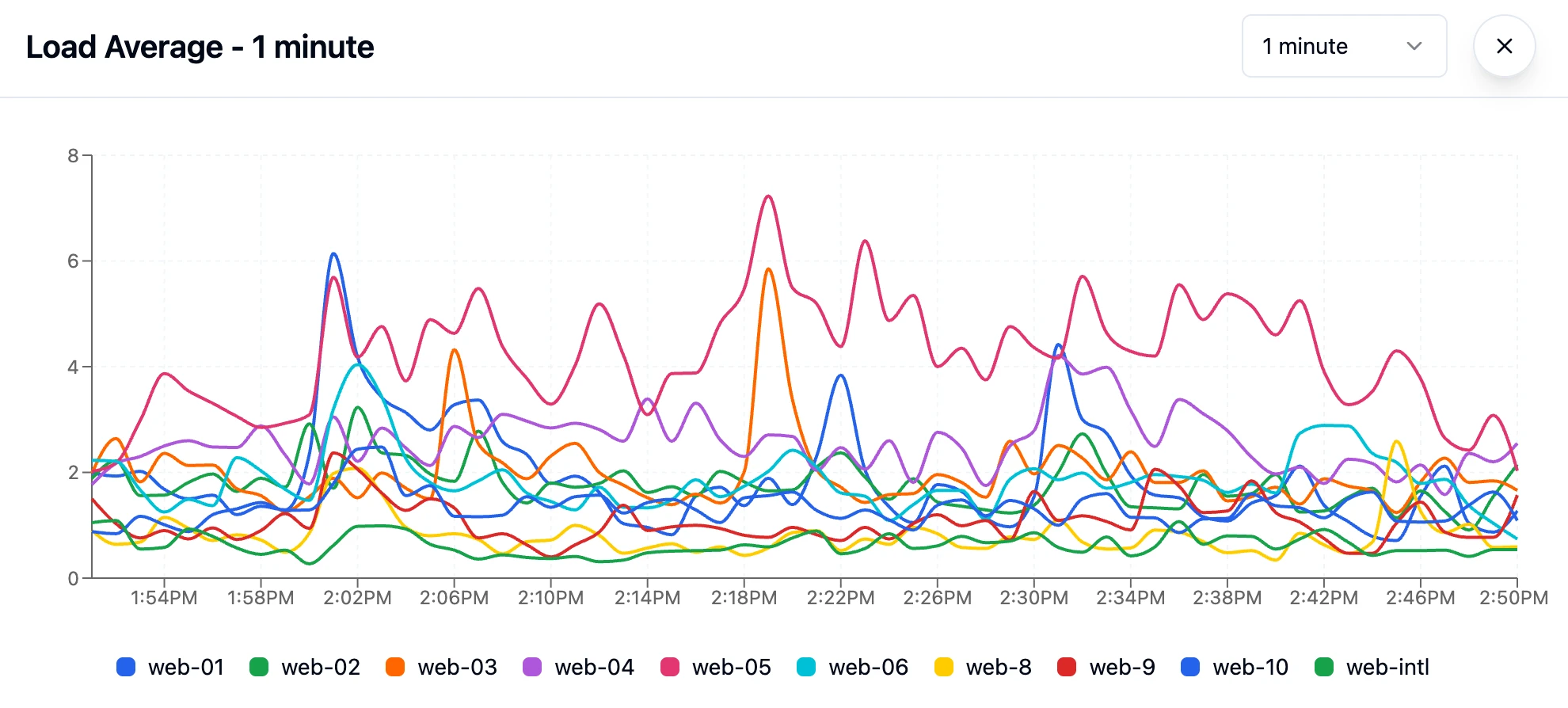
Quick shameless plug here, I recently moved my server load monitor tool out to it's own service, in case you want these charts for your servers. Still very early, it'll be free while it's in beta. WebServerCharts
So I ran my "log hunter" script to analyze the log files on the server and return the most recent top IP's by total request duration.
Top IPs by total time (last 50 periods):
IP Address Requests Total Time Avg Time Mins Sites
-----------------------------------------------------------------------------------------------
79.132.192.x 1940 2840.16 1.46 41
66.249.66.x 480 632.17 1.32 49
66.249.72.x 125 305.53 2.44 49
66.249.66.x 101 236.89 2.35 49Sure enough, the top user over the past 50 minutes was pretty consistent, followed by 3 Google crawler IPs. Checking the logs, it was pretty clear they were hitting the wp-login endpoint consistently. Here is a snippet of 1 second worth of logs from this IP.
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10952 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.106 3.123 200 3.124 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.153 3.159 200 3.160 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10952 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.044 3.065 200 3.065 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.048 3.058 200 3.059 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.113 3.136 200 3.137 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "POST /wp-login.php HTTP/1.0" 401 0 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.005 0.005 401 0.005
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "POST /wp-login.php HTTP/1.0" 401 0 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.010 0.010 401 0.011
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.216 3.227 200 3.226 -
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "POST /wp-login.php HTTP/1.0" 401 0 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.008 0.008 401 0.009
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "POST /wp-login.php HTTP/1.0" 401 0 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.003 0.003 401 0.007
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "POST /wp-login.php HTTP/1.0" 401 0 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.004 0.004 401 0.006
79.132.192.x - - [29/Oct/2025:19:44:36 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.371 3.380 200 3.380 -The pattern is very clear, the bot is retrieving via the GET (presumably to obtain the recaptcha token) and then submitting a corresponding POST. You can see by the timings here that I'm already blocking the POST efficiently, but those GET calls are really what was slowing things down. The POST's are being blocked by a custom security plugin I added to prevent wasting CPU time on brute force bots like this.
I was curious how this started, so I checked the first few calls by this IP
79.132.192.x - - [29/Oct/2025:18:34:05 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.590 1.599 200 1.599 -
79.132.192.x - - [29/Oct/2025:18:49:02 +0000] "GET /wp/wp-login.php HTTP/1.1" 404 47 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.010 0.010 404 0.010 -
79.132.192.x - - [29/Oct/2025:18:58:24 +0000] "GET /wp-json/wp/v2/users HTTP/1.1" 200 7054 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.721 1.729 200 1.729 -
79.132.192.x - - [29/Oct/2025:18:59:03 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.270 2.301 200 2.302 -
79.132.192.x - - [29/Oct/2025:18:59:03 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.337 2.352 200 2.351 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.763 2.782 200 2.782 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.847 2.855 200 2.856 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10952 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.931 2.950 200 2.951 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.940 2.957 200 2.956 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.995 3.005 200 3.006 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.013 3.022 200 3.023 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10952 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.042 3.051 200 3.052 -
79.132.192.x - - [29/Oct/2025:18:59:04 +0000] "GET /wp-login.php HTTP/1.0" 200 10953 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 3.122 3.131 200 3.131 -Seems like they pulled the user list first, presumably to try some dictionary attack the known users. This is one of the reasons I generally prefer to block the WP API, no good comes from exposing it!
Worth noting, I saw the exact same type of attack yesterday from another IP in Czech Republic (the one today was in Iran).
217.75.221.x - - [28/Oct/2025:23:27:07 +0000] "GET /wp-login.php HTTP/1.1" 200 2138 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.940 0.940 200 0.942
217.75.221.x - - [28/Oct/2025:23:34:38 +0000] "GET /wp/wp-login.php HTTP/1.1" 404 36 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.004 0.004 404 0.003
217.75.221.x - - [28/Oct/2025:23:37:47 +0000] "GET /wp-json/wp/v2/users HTTP/1.1" 200 5184 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 0.004 0.004 200 0.002
217.75.221.x - - [28/Oct/2025:23:38:03 +0000] "POST /xmlrpc.php HTTP/1.1" 404 193 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" - - - - 0.000 -
217.75.221.x - - [28/Oct/2025:23:38:23 +0000] "GET /wp-login.php HTTP/1.1" 200 2134 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.592 1.592 200 1.592
217.75.221.x - - [28/Oct/2025:23:38:23 +0000] "GET /wp-login.php HTTP/1.1" 200 2138 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.932 1.932 200 1.931
217.75.221.x - - [28/Oct/2025:23:38:25 +0000] "POST /wp-login.php HTTP/1.1" 200 2318 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 1.996 1.996 200 1.995
217.75.221.x - - [28/Oct/2025:23:38:26 +0000] "POST /wp-login.php HTTP/1.1" 200 2323 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 2.148 2.148 200 2.151
217.75.221.x - - [28/Oct/2025:23:38:23 +0000] "GET /wp-login.php HTTP/1.1" 200 2134 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.576 1.576 200 1.576
217.75.221.x - - [28/Oct/2025:23:38:25 +0000] "GET /wp-login.php HTTP/1.1" 200 2138 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 2.416 2.416 200 2.414
217.75.221.x - - [28/Oct/2025:23:38:26 +0000] "POST /wp-login.php HTTP/1.1" 200 2317 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.672 1.672 200 1.671
217.75.221.x - - [28/Oct/2025:23:38:26 +0000] "POST /wp-login.php HTTP/1.1" 200 2318 "https://redacted/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 1.596 1.596 200 1.594Looking here, it's clear that the user agent is consistent even though the IP's are from two very different areas
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36
Looking a bit more, a third from today, which appears to be coming from Iran.
185.128.139.x - - [29/Oct/2025:12:39:33 +0000] "GET /wp-login.php HTTP/1.1" 200 5014 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.212 1.212 200 1.211
185.128.139.x - - [29/Oct/2025:12:56:08 +0000] "GET /wp/wp-login.php HTTP/1.1" 404 36 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 0.008 0.008 404 0.005
185.128.139.x - - [29/Oct/2025:12:59:17 +0000] "GET /wp-json/wp/v2/users HTTP/1.1" 200 538 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 1.264 1.264 200 1.261
185.128.139.x - - [29/Oct/2025:12:59:35 +0000] "POST /xmlrpc.php HTTP/1.1" 404 193 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" - - - - 0.000 -
185.128.139.x - - [29/Oct/2025:12:59:55 +0000] "GET /wp-login.php HTTP/1.1" 200 5020 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.129 1.129 200 1.131
185.128.139.x - - [29/Oct/2025:12:59:55 +0000] "GET /wp-login.php HTTP/1.1" 200 5014 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.165 1.165 200 1.165
185.128.139.x - - [29/Oct/2025:12:59:55 +0000] "GET /wp-login.php HTTP/1.1" 200 5013 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.157 1.157 200 1.153
185.128.139.x - - [29/Oct/2025:12:59:56 +0000] "POST /wp-login.php HTTP/1.1" 200 5143 "https://redacted3/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 1.168 1.168 200 1.168
185.128.139.x - - [29/Oct/2025:12:59:56 +0000] "POST /wp-login.php HTTP/1.1" 200 5156 "https://redacted3/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 1.220 1.220 200 1.220
185.128.139.x - - [29/Oct/2025:12:59:56 +0000] "POST /wp-login.php HTTP/1.1" 200 5142 "https://redacted3/wp-admin/" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.016 1.256 1.256 200 1.257Another one today that was from Argentina, on a site where the xmlrpc is open due to client request
186.189.235.x - - [29/Oct/2025:18:27:52 +0000] "GET /wp-login.php HTTP/1.1" 200 3507 "https://www.google.com" "Mozilla/5.0 (X11; Linuxx86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.004 0.684 0.684 200 0.683
186.189.235.x - - [29/Oct/2025:18:36:01 +0000] "GET /wp/wp-login.php HTTP/1.1" 404 47 "https://www.google.com" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.032 0.032 404 0.032
186.189.235.x - - [29/Oct/2025:18:39:33 +0000] "GET /wp-json/wp/v2/users HTTP/1.1" 200 1319 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.004 0.004 200 0.004 HIT
186.189.235.x - - [29/Oct/2025:18:39:52 +0000] "POST /xmlrpc.php HTTP/1.1" 200 223 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.624 0.624 200 0.628
186.189.235.x - - [29/Oct/2025:18:40:10 +0000] "POST /xmlrpc.php HTTP/1.1" 401 0 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.012 0.060 0.060 401 0.060
186.189.235.x - - [29/Oct/2025:18:40:10 +0000] "POST /xmlrpc.php HTTP/1.1" 401 0 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.012 0.072 0.072 401 0.071
186.189.235.x - - [29/Oct/2025:18:40:10 +0000] "POST /xmlrpc.php HTTP/1.1" 401 5 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.020 0.092 0.092 401 0.092
186.189.235.x - - [29/Oct/2025:18:40:11 +0000] "POST /xmlrpc.php HTTP/1.1" 200 223 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36" 0.000 0.988 0.988 200 0.989So the clearest signature here is the user agent, followed by a 3 request pattern of GET /wp-login.php -> GET /wp/wp-login.php -> GET /wp-json/wp/v2/users -> POST /xmlrpc.php. Followed by xmlrpc POSTs if available, otherwise GET->POST cycles on wp-login.php. The country of origin appears to be all over including CZ, IR, AR
A quick grep to find any offending IPs potentially (assuming nginx) would be to run this grep:
grep -ri "GET /wp/wp-login.php" /var/log/nginx/*.log | grep "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/140.0.0.0 Safari/537.36"My goal is to call out new bots when I see them, so hopefully this was informational.